
The cybersecurity software Crowdstrike Falcon is replacing SentinelOne on the majority of CoreImage PCs this week, November 15-19 (kiosk computers were updated in October).
This change requires a restart to remove SentinelOne from your device. Users will have two opportunities to defer the restart so they can choose an optimal time to do so.
About CrowdStrike Falcon
To improve Michigan Medicine’s defenses against cyber attacks and ransomware, we are migrating to an enhanced endpoint protection software powered by CrowdStrike Falcon. Migrating to CrowdStrike provides a common platform across all of U-M to allow for better threat identification, mitigation, and incident response activities.
User Impacts
When SentinelOne is removed, a restart is required to complete the uninstallation process. Migration to CrowdStrike will occur for Michigan Medicine CoreImage PCs November 1-19, 2021, with the majority of PCs migrating November 15-19.
What to Expect
Restarting a CoreImage PC will allow CrowdStrike Falcon to be registered as the primary endpoint agent for your workstation. Below are examples of a series of messages users can expect to see.
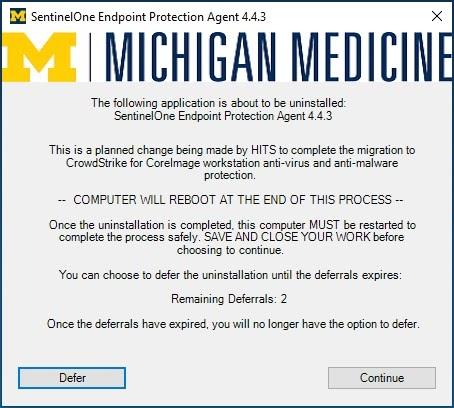
If the computer is in-use at the time it is targeted for the SentinelOne uninstallation, logged in users will see the following dialog first. Users can expect the option to defer the restart twice.
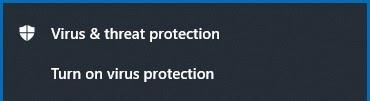
Users may see this notification from Windows. This is an expected action.
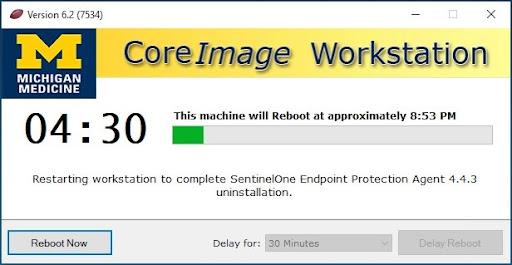
Users will receive a 5-minute, non-deferrable restart prompt at the end.
How Crowdstrike Falcon works
Once CrowdStrike Falcon is registered as the primary threat protection software, it will run in the background and there will be no system tray icon as with SentinelOne. If a threat is detected on the device, the user is alerted via a pop-up message and the agent intervenes and blocks the process.
Examples of popup messages are provided below. If you see a popup, you do not need to take any action. The Cybersecurity Operations teams will be alerted behind the scenes and will monitor and evaluate the threat.
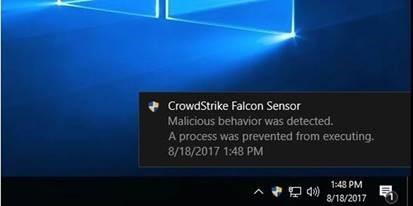
A example of when CrowdStrike intervenes and blocks a process:
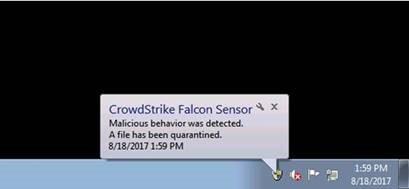
A example of when CrowdStrike intervenes and quarantines a file:
If you experience any issues, please visit help.medicine.umich.edu and submit a ticket. The IA Cybersecurity team will work to address any issues you may have.
For more about the CrowdStrike endpoint protection software, visit the U-M Safe Computing website.
